As a Platform Engineer, I’ve had extensive experience with various tools designed to bolster our digital security. Recently, I’ve been focusing on two particular solutions: Trivy and Gitleaks. This article aims to provide a professional comparison of these tools, specifically in the context of password scanning and repository security.
For months, I’ve integrated Trivy into our pipelines, primarily utilizing its capability to scan container images for vulnerabilities within their libraries. I was aware of Trivy’s “password scanning” functionality, but recent events prompted me to investigate this feature more thoroughly.
After attending a talk on “Securing your Git Repositories with Password Scanning,” I decided to put Trivy to the test. The results were eye-opening. Upon deliberately hardcoding a password into a file and running a Trivy scan across the filesystem, I was surprised to find that Trivy failed to detect the plaintext password.
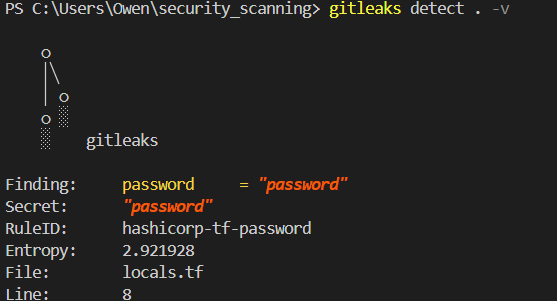
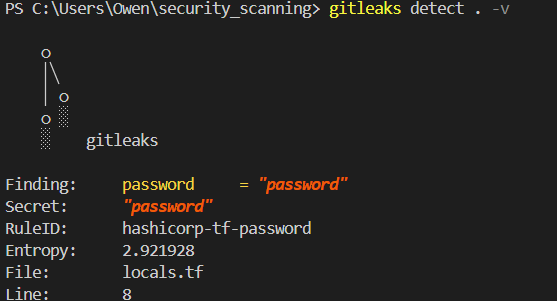
This discovery led me to explore Gitleaks, an open-source tool specifically designed for password scanning. Running Gitleaks on the same filesystem immediately flagged the hardcoded password, demonstrating its effectiveness in this particular use case.
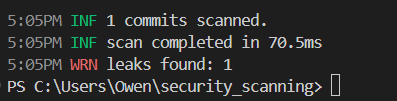
To further evaluate Gitleaks’ capabilities, I committed the code with the hardcoded password, pushed it upstream, and removed it locally. Using Gitleaks with the ‘–no-git’ flag (which scans the code without examining git history) yielded no results, as expected.
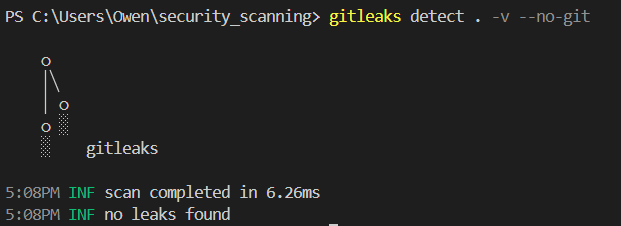
However, running Gitleaks without this flag revealed its true power: it detected the password in the git history and provided metadata for the exact commit containing the sensitive information.
Gitleaks shines when it comes to uncovering historical security oversights, making it an invaluable tool for retrospective audits and targeted fixes. However, we need to tread carefully when addressing these past issues in git repositories. Modifying old commits is risky business – it can throw off the entire git history from that point on. When we do stumble upon exposed credentials, the best move is to invalidate and rotate them right away.
Implementation
To stay ahead of the game, it’s worth considering a password scan as part of your CI/CD pipeline. This proactive step can catch potential leaks before they make it into the main codebase. Gitleaks’ GitHub Actions integration is convenient here, offering an automated way to block compromised code from being pushed.
While Trivy and Gitleaks might seem similar at first glance, they each bring something unique to the table. Trivy excels at scanning images for vulnerabilities, while Gitleaks is your go-to for securing codebases, with or without GitHub pre-commit hooks.
Conclusion
Going forward, I’m planning to implement both tools in my projects. By leveraging their strengths, we can build a more robust security setup. This two-pronged approach lets us benefit from Trivy’s thorough image scans while tapping into Gitleaks’ powerful code and commit analysis to keep credential leaks at bay.
We need to stay on our toes as security engineers, always tweaking our tools to keep up with new threats. By using Trivy and Gitleaks together, we’re making real progress in protecting our digital resources and keeping our code repositories clean.
